Tun2Tap: What It Is & How It Works for Network Tunneling
In the world of networking, tunneling plays an important role in guaranteeing secure and efficient data transmission. One of the technologies used for this purpose is Tun2Tap, a versatile tool that facilitates the bridging of virtual network interfaces. This article explores what Tun2Tap is, how it works, and its applications in network tunneling.
What is Tun2Tap?
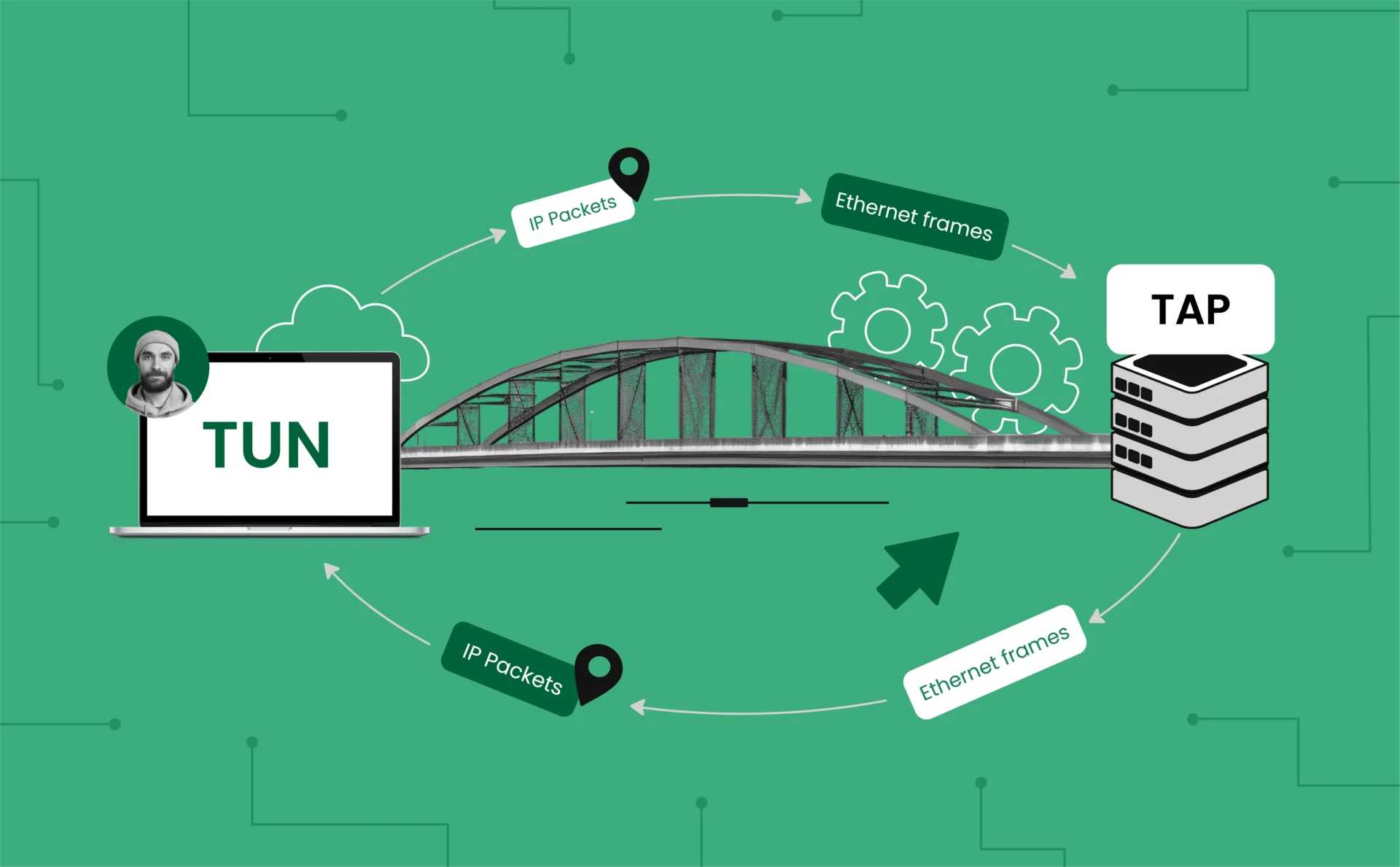
Tun2Tap is an application that provides intercommunication of TUN (network layer) virtual interfaces and TAP (data link layer) virtual interfaces. The virtual interfaces are widely used in VPNs, network simulating, and other security tasks. The key function of Tun2Tap is to bridge these virtual interfaces to make traffic originating from a TUN interface routed over a TAP interface and vice versa.
Understanding TUN and TAP interfaces
Before delving into how Tun2Tap works, it is necessary to understand the two key components it interacts with: TUN and TAP interfaces.
TUN (Network Layer Interface)
TUN stands for “network TUNnel.” It operates at the network layer (Layer 3 of the OSI model) and is responsible for handling IP packets. TUN devices are used to create point-to-point network tunnels, which are commonly employed in VPN solutions.
TAP (Data Link Layer Interface)
TAP, on the other hand, stands for “network TAP.” It functions at the data link layer (Layer 2) and is used for handling Ethernet frames. TAP devices are used when full Ethernet communication is needed, such as in bridged networks or VLAN configurations.
How Tun2Tap works
Tun2Tap acts as a bridge between TUN and TAP interfaces, converting network-layer packets into data-link layer frames and vice versa. The process follows these steps:
- Packet reception: A network packet enters the TUN interface.
- Conversion: Tun2Tap converts the IP packet into an Ethernet frame.
- Transmission: The Ethernet frame is sent through the TAP interface.
- Reverse process: When an Ethernet frame is received via the TAP interface, Tun2Tap extracts the IP packet and forwards it to the TUN interface.
This process allows easy communication between applications using different networking layers, making Tun2Tap highly valuable in various network configurations.
Applications of Tun2Tap
1. VPN implementations
Tun2Tap is widely used in VPN solutions to allow secure tunneling of network traffic. By converting TUN packets into TAP frames, it allows VPN services to function in environments where Ethernet-level networking is required.
2. Network simulation and testing
In network simulation and testing scenarios, Tun2Tap facilitates the creation of complex network topologies. It allows researchers and developers to test different networking configurations without requiring physical hardware.
3. Security and penetration testing
Tun2Tap plays an important role in cybersecurity by allowing traffic manipulation for security analysis and penetration testing. Ethical hackers use it to simulate attack scenarios and evaluate network vulnerabilities.
4. Cloud and virtualization environments
With the rise of cloud computing and virtualized infrastructures, Tun2Tap is utilized to create virtual network bridges that enhance communication between different virtual machines and containers.
How to set up Tun2Tap
Prerequisites
Before setting up Tun2Tap, guarantee that you have:
- A Linux-based system (Tun2Tap is commonly used on Linux environments)
- Administrative or root privileges
- The Tun2Tap software installed
Step-by-step guide
- Install Tun2Tap
- Create a TUN interface
- Create a TAP interface
- Bridge TUN and TAP using Tun2Tap
- Verify network communication
Once configured, your system will have an active TUN-to-TAP bridge, enabling easy network tunneling.
Best practices for using Tun2Tap
- Secure your tunnels: Always use encryption and authentication mechanisms to protect your network traffic.
- Monitor network traffic: Use network monitoring tools to analyze traffic passing through your Tun2Tap setup.
- Optimize performance: Fine-tune buffer sizes and packet handling settings to enhance performance in high-traffic environments.
Common issues and troubleshooting
Issue 1: Tun2Tap not found
Solution: Ensure that the software is installed correctly using package managers like apt or yum.
Issue 2: Interface not responding
Solution: Verify that the interface is up and running by using ifconfig or ip link show.
Issue 3: Network traffic not passing through
Solution: Check firewall rules and routing configurations to ensure packets are correctly forwarded.
Advanced use cases of Tun2Tap
1. Bridging networks for IoT devices
IoT deployments often require safe communication between devices using different network protocols. Tun2Tap allows easy connectivity by bridging TUN and TAP interfaces.
2. Enabling secure remote access
Organizations use Tun2Tap to set up secure remote access solutions where Ethernet connectivity is required across geographically distributed locations.
3. Enhancing containerized network environments
With the rise of containerized applications, Tun2Tap helps in setting up network tunneling solutions that guarantee efficient inter-container communication.
Performance optimization tips for Tun2Tap
To guarantee Tun2Tap performs efficiently, consider these optimization strategies:
- Adjust buffer sizes: Increasing the buffer size for packet handling can reduce latency and packet loss.
- Enable multithreading: Utilize multi-threaded processing where possible to improve throughput.
- Use compression: Apply data compression techniques to minimize bandwidth usage when transmitting data through the tunnel.
- Monitor network latency: Identify bottlenecks by using tools like Wireshark to analyze packet flow.
- Reduce overhead: Minimize unnecessary network overhead by fine-tuning protocol settings and removing redundant encapsulation layers.
Use cases in enterprise Networking
Tun2Tap is widely used in enterprise environments for various applications:
- Secure communication: Large organizations use Tun2Tap to establish encrypted and private communication channels for internal data transfer.
- Remote access solutions: Businesses configure Tun2Tap tunnels to enable employees to securely access corporate networks from remote locations.
- Network segmentation: Enterprises leverage Tun2Tap to create segmented network infrastructures, improving security by isolating sensitive systems.
- Testing & development: IT teams utilize Tun2Tap for testing new network configurations before deployment in a production environment.
Final Verdict
Tun2Tap is a powerful TUN and TAP bridging utility that allows easy network tunneling between various applications. Employed in VPN solutions, network testing, or security studies, Tun2Tap is a critical part of modern networking. Through the understanding of its setup, best practices, and expert uses, users can leverage its full potential to fine-tune their network configuration.
For those looking to explore secure network tunneling further, Tun2Tap is an excellent point to begin from. With careful configuration and sensible practices, it can actually extend your networking considerably.